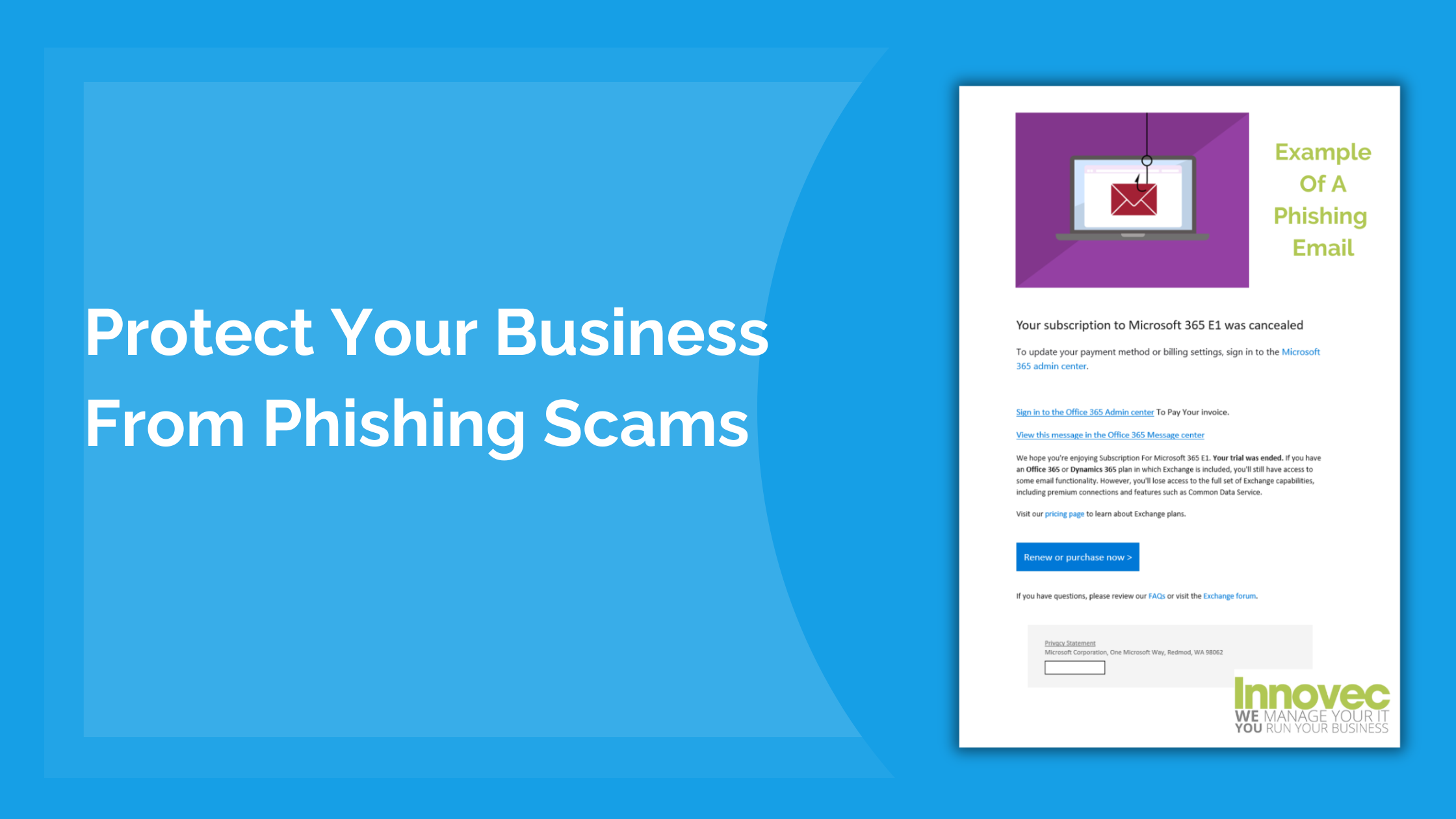
How To Protect Your Business From Phishing Scams
Some Cybersecurity attacks can sneak past spam filters undetected because of how sophisticated and realistic they appear. These attacks are called Phishing.
Instead of Fishing for fish, they are PHISHING for your log in credentials and credit card numbers. They often to hold the data for ransom or for Identity theft purposes.
A phishing attack can be carried out in mass or targeting to a specific company. It’s not just your inbox you need to watch, phishing can be done through text message and social media messaging.
This article will include common examples, how to recognise a phishing message/email, tips on avoidance and what to do if anyone in your company receives a phishing email or falls victim.
The Various Ways Phishing Is Carried Out
Below are some common examples of ways cybercriminals Phish for your credentials;
- PayPal Scam
- Google Docs
- “Message” From HM Revenue
- Dropbox Scam
- Amazon Voucher Scam
- “Fake Invoice Scam” (This is the most common template out there)
- Email Account Upgrade Email
- “Your Password Needs Reset” Email
- Advance-Fee Text Message
This Phishing Signs To Look Out For
Although Phishing scams are getting increasingly more sophisticated and realistic. To avoid falling victim, there are some signs to look out for.
- Public Email Domains
- Misspelled Domain Names
- Bad Grammar And Spelling
- Sense Of Urgency
- Suspicious Attachments/Links
Tips To Avoid Falling Victim To Phishing Attacks
Below are some tips on how to avoid falling victim to phishing attacks:
Recognise the signs of Phishing – Phishing emails often have spelling and grammar errors, use generic greetings, create a sense of urgency, or ask for sensitive information. They may also have suspicious links or attachments, or come from unfamiliar or spoofed email addresses.
Don’t respond to a Phishing Email – If you receive a suspicious message, do not reply or click on any links or attachments. This can expose your device to malware or confirm your email address to the scammer.
Use security software and update it regularly – You can protect your computer and cell phone by using security software that can detect and block phishing attempts. Make sure to set the software to update automatically so it can deal with any new security threats.
Report suspicious messages to your IT Provider – By reporting suspicious emails to your IT provider, they will help by blocking the sender as well as any similar messages in the future, and warn other users within your company about the threat.
How We Can Help You
We can apply the following changes to help mitigate some of the examples above.
Add a professional spam filter such as ProofPoint or Spam Titan – this will help filter out more of these types of attacks by intelligently looking through the content of the incoming e-mail
Add a notification to all externally received e-mails – this will highlight to all users that the e-mail is from an external source and not from “the boss”
End user education – we can send out test e-mails to your users to help educate with real-world examples
If you could benefit from any of the help above, get in touch with our Innovec team. We will be happy to arrange a 10 minute call at a time which suits you, for a chat about how we can help and offer some advice.
